What is Single Sign-On and How Does It Work
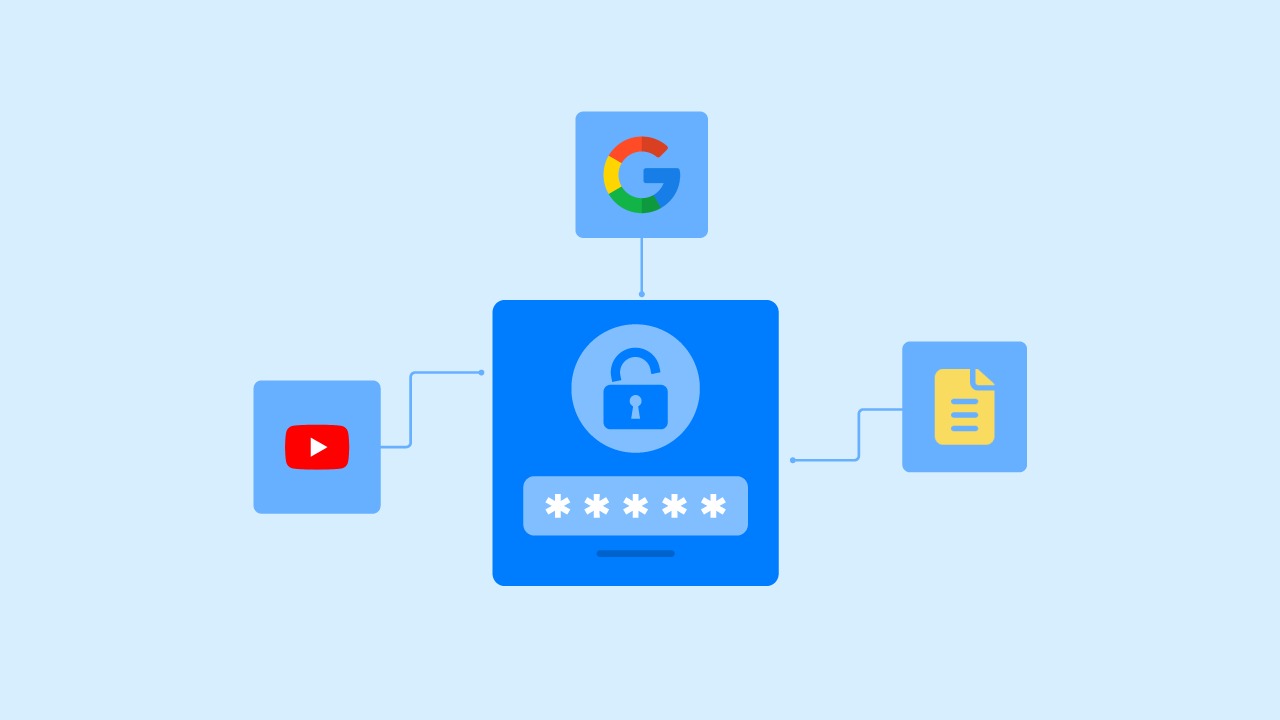
User experience is integral to boosting business revenue. When potential customers visit a website, the goal is to lead them smoothly towards a transaction. However, repeated login requests can lead to increased frustration, potentially pushing them to exit.
This is where Single Sign-On (SSO) comes into play. By facilitating just one initial login, SSO ensures users can seamlessly access multiple connected applications, greatly enhancing the overall user experience and promoting sustained engagement.
What is Single Sign-On (SSO)?
Single Sign-On (SSO) serves as a gateway to effortless user authentication. Imagine only needing one key to unlock multiple doors. With SSO, users input their credentials just once to gain access to a host of interconnected websites and applications. This mechanism is an integral component of Identity and Access Management (IAM)—a comprehensive framework that dictates how users identify themselves and gain access to specific resources.
Also, check out our article on: What is Unified Access Management and Why Do Growing Companies Need it?
Consider Single Sign-On as a universal library card. Instead of requiring a distinct card for every library branch, this single card allows you to borrow books from any branch, expanding your reading options exponentially. Similarly, SSO unifies access across various applications used by the same company.
One of the most recognizable implementations of SSO is Google’s G-suite. Once you’re logged into your Google account, a plethora of associated services, like YouTube and Google Docs, become instantly accessible.
Although many associate SSO primarily with end-user authentication, it’s important to note its significance in Business-to-Employee (B2E). Numerous enterprises adopt SSO for their workforce, streamlining access. For instance, an employee logging into their company portal might find they’re simultaneously logged into tools like Slack and Zoom, all tied to their unique employee ID. Notably, an average of 68 percent of employees have to switch between ten apps every hour, making the case for SSO’s efficiency in reducing the time spent on switching between different applications.
How Does It Work?
SSO can be executed using various protocols, such as OpenID Connect, SAML, and the like. While the way it functions might vary among these protocols, the core principle driving them remains consistent.
When a user first tries to log in, the application sends them over to the identity provider. An identity provider is a service that stores and manages user identities on behalf of an application.
For end users, common identity providers include Google and Facebook.
Enterprise identity providers include Microsoft Active Directory, Azure AD, LDAP, and G Suite. This provider then looks for a Single Sign-On (SSO) cookie in the user’s browser. Since it’s the user’s first time visiting and there’s no SSO cookie, they’re asked to log in using one of the connections configured by the identity provider.
After the user logs in successfully, the identity provider creates an SSO cookie for future visits and sends the user back to the application with a token that has their identity details.
When a user successfully logs in using the SSO system, they are provided with a token. As they navigate to a different page, this token acts as proof that they’ve already authenticated, eliminating the need to log in again. This process can be facilitated through various mechanisms, including the Security Assertion Markup Language (SAML) and Open Authorization (OAuth).
Breaking it down, SAML primarily confirms who the user is (authentication), while OAuth determines which assets or data a user can access (authorization).
Furthermore, many SSO systems come equipped with a feature called single log-out (SLO). Essentially, when a user logs out from one application, they’re automatically signed out from all connected applications.
SSO Security Risks and Solutions
With SSO, imagine a user’s login details as a master key, giving access to numerous applications. However, just as a master key can be dangerous in the wrong hands, so too can a password. The more gates it can open, the higher the potential risk of it falling into the clutches of cybercriminals.
This risk amplifies when users recycle passwords across platforms. A survey by last pass revealed that 91% of the survey respondents professed to understand the high risk of using the same passwords across multiple accounts, and 59% of them said they did so anyway. Credential Stuffing is a cyber tactic where hackers use stolen passwords from one breach to infiltrate other sites, and has emerged as a substantial security threat. Its effectiveness is largely because of the user’s tendency to employ identical passwords for diverse purposes.
SSO can actually act as a protective measure against such risks. By diminishing “password fatigue”, it indirectly encourages users to diversify their passwords. The logic is simple: fewer passwords to remember often translates to less repetition and a decreased reliance on old, familiar codes.
However, relying solely on SSO for security may not be the wisest move. Combining it with robust authentication measures, like multifactor authentication (MFA) can decrease breach risks by adding an extra security layer. As of January 2023, MFA adoption climbed to 64% among Okta workforce users, emphasizing the importance and adoption rate of such security measures. When a user’s behavior seems out of the ordinary, like accessing sensitive data, MFA prompts them for extra proof of identity. This might involve a verification code sent via email or phone, or even biometric verifications such as a fingerprint scan.
While MFA is undoubtedly secure, implementing it for every single login is not a smart move either. This is where contextual MFAs enable companies to tailor-fit authentication requirements. For instance, when a user logs in from a new device, MFA could trigger a verification process, ensuring optimal security without constant interruptions.
Last but not least, another solution for safeguarding SSO is to smartly regulate session durations. Take a banking app: due to its sensitive nature, it might have a short session, logging users out after brief inactivity. Contrast this with a video streaming platform, where rigorous access checks aren’t as critical, allowing users prolonged sessions before prompting for identity verification again.
6 Best Single Sign-On Tools
Choosing the right SSO tool is pivotal to ensure a seamless user experience. The right SSO tool not only streamlines access but also fortifies the digital boundaries against potential security threats. Here are some of the top SSO tools that are recognized for their performance, security, and ease of integration:
Okta
Okta Workforce Identity is a robust Single Sign-On (SSO) solution engineered to streamline user access and authentication across a myriad of applications and services within an organization. With Okta SSO, your team can seamlessly and securely log in to their work accounts without having to remember numerous passwords.
Okta SSO simplifies user lifecycle management by automating the process of adding and removing user accounts. When employees join or leave the organization, Okta adjusts access to applications accordingly, reducing administrative tasks.
Key Features:
- Centralized Identity Management: Okta SSO provides a centralized location for managing user identities, which helps in providing or revoking access to applications simpler as roles change, ensuring employees have appropriate access at all times.
- Multi-Factor Authentication (MFA): Okta supports different MFA methods like SMS, push notifications, and biometrics to ensure that only the right individuals can access important resources.
- Adaptive Access Policies: Okta’s adaptive access policies allow the setup of context-based rules for user access, meaning permissions can be changed based on factors such as location, device, or behavior, which adds another level of security.
- Passwordless Authentication: Okta SSO features passwordless authentication options like biometrics and one-time passcodes, moving away from traditional password policies and lowering the risk associated with password-related vulnerabilities.
Gartner Reviews: 4.5/5
Jump Cloud
JumpCloud’s Cloud Directory platform stands as a universal directory meticulously crafted to ease user authentication and bolster security across your organization’s diverse resources. With a spotlight on Single Sign-On (SSO), it invites you to centralize access control, smooth out workflows, and fortify security measures.
With JumpCloud, integrating your organization’s applications and services with SSO becomes easier. Users can securely traverse through all their authorized resources using a single set of credentials, elevating convenience while maintaining a strong security stance.
Key Features
- Unified Access Control: JumpCloud’s Cloud Directory serves as a centralized hub for user access management. It brings together user identities across different systems, applications, and devices.
- Enhanced Security: It provides strong security features like multi-factor authentication (MFA) to help guard against unauthorized access attempts. Plus, you can set up strong password rules and watch user activities to catch possible threats.
- Cross-Platform Compatibility: JumpCloud is compatible with many operating systems including Windows, macOS, and Linux. This way, users can use SSO on their preferred devices and platforms.
- User Self-Service: Give your users the ability to help themselves with self-service features. They can reset their passwords and update their profiles on their own, which eases the load on IT support and improves overall user satisfaction.
- Automated Provisioning & Deprovisioning: With JumpCloud, you can set up automatic adding and removing of user accounts, making sure access is given or taken away quickly and correctly.
Gartner Rating: 4.5/5
OneLogin
OneLogin provides a top-notch SSO solution making user authentication and access management easier. With OneLogin, your IT team can cut down on the hassle of handling many usernames and passwords across different applications. Instead, users can get into all their authorized systems using just one set of login details.
In addition, OneLogin Cloud Directory gives easy access to new employees access, and takes away access from those who are leaving, lowering the chances of unauthorized access.
Key Features:
- Unified Access Control: OneLogin offers a centralized dashboard allowing IT managers to monitor and control user access to all applications and services easily. This unified approach ensures that only the right people can get to sensitive data and resources.
- Multi-Factor Authentication (MFA): MFA options like biometrics, SMS verification, or token-based authentication add an extra layer of security. OneLogin makes sure that only approved users can access your systems.
- Directory Integration: Easily sync your current directory services (like Active Directory or LDAP) with OneLogin Cloud Directory keeping user identities and access permissions updated across all applications.
- Single Logout: With OneLogin, users can log out from all linked applications with just one click, making things secure and convenient.
- Customizable Policies: it shapes access control policies to fit your organization’s unique needs by Setting up rules based on roles, departments, or other factors to ensure the right people can access the right resources.
- Audit Trail and Reporting: Stay updated with thorough audit logs and reports. Monitor user activities, spot possible security threats, and show compliance effortlessly.
Gartner Rating: 4.⅘
Keeper Security
Keeper Security offers SSO solution crafted to simplify access management across organizations. It allows your teams to centrally manage user access to applications and eliminate the risk of remembering passwords and security breaches.
It offers a smooth integration process and is adaptable to the changing technology without compromising on security.
Key Features:
- Enhanced Security: it enforces strong password policies, offers MFA, and provides real-time monitoring ensuring that your sensitive data is protected against any security threats.
- User-Friendly Interface: its intuitive dashboard offers a clear overview of user activity, security events, and compliance status prioritizing user experience for the users.
- Compliance and Reporting: it has a straightforward auditing process. it provides comprehensive reporting tools to keep track of user access, changes, and security events, proactively addressing potential security issues.
Gartner Rating: 5/5
Ping Identity
Ping Identity’s powerful single sign-on solution streamlines user authentication processes, enhances security, and boosts productivity. It allows the employees to access all their necessary applications and services with a single set of login credentials.
Key Features
- Centralized Access Control: it allows simplified onboarding and offboarding processes, making sure that access is granted and revoked promptly.
- Integration Capabilities: It seamlessly integrates with a plethora of applications, including cloud-based and on-premises systems. This means you can keep using the apps you want with an extra layer of security and convenience.
- Compliance Made Easy: The solution enforces access policies and provides detailed audit logs for compliance reporting.
- User Self-Service: users can easily reset passwords, manage their profiles, and access the self-service feature.
- Scalability: Ping Identity’s SSO tool scales as your company grows. you won’t need to overhaul your authentication processes – simply expand your Ping Identity solution to accommodate new users and applications.
Gartner rating: 4.4/5
Cisco Secure Access by Duo
Cisco Secure Access is a cloud app engineered to enhance your organization’s security and user experience. It streamlines access management by offering employees a seamless single sign-on (SSO) experience.
Cisco eliminates the user’s requirement to remember multiple passwords by giving them access to various applications and resources with just one set of credentials. Not just that, Cisco Secure Access by Duo is highly compatible. It can easily integrate with your identity providers, such as Active Directory or LDAP, and scales as you grow.
Key Features
- Unified Access Control: The app offers a universal directory to manage user access rights across networks and cloud applications ensuring authorized access to critical resources.
- Multi-Factor Authentication (MFA): It adds a layer of protection beyond passwords. Users can verify their identity through various methods, such as mobile push notifications, SMS, or hardware tokens, making it nearly impossible for unauthorized users to gain access.
- Comprehensive Application Support: It is compatible with a wide range of on-premises and cloud-based applications. Whether you use Microsoft 365, Salesforce, or custom-built apps, SSO can be seamlessly integrated, improving accessibility without compromising security.
- Mobile Device Management (MDM) Integration: Securely manage and monitor mobile device access to corporate resources. This pre-built integration ensures enforcement of security policies making sure that only trusted devices can seamlessly access sensitive data.
Gartner Rating: 4.5/5
How to implement SSO in your organization?
With the implementation of Single Sign-On, users can enjoy the convenience of remembering just a single password for all their applications and devices. However, its implementation and integration of SSO tools require expertise.
Codup is your tech partner specializing in deploying SSO solutions to meet your organization’s unique needs. Our approach emphasizes transparent communication, unwavering commitment to excellence, and a proven track record of delivering results, making us the ideal partner for your next project.
Connect with experts at CODUP for top-notch digital transformation services.